With more than 70% of all attacks now harming web applications, organizations do their best to secure their systems and protect their web actives.
Web application firewalls are really reliable tools made to bring external security layer, increasing the protection level, detects and prevents attacks before they reach web-based software systems.
When we talk about ModSecurity, we need to know that is an open-source web-based firewall application (or WAF) supported by different web servers: Apache, Nginx, Litespeed and IIS. One of the application layer protections we have to use in order to inrease the security levels in our servers.
Why we use ModSecurity and how does protect us?
ModSecurity module made and setup to protect your web applications from various attacks. It uses flexible rule engine in order to perform both simple and complex operations. The Core Rule Set (CRS) is main part of it and the idea is to have various rules for:
- cross website scripting
- bad user agents
- SQL injection
- trojans
- session hijacking
- and many more exploits
Common errors that ModSecurity causes
One of the most common error triggered by a mod_security rule on our shared hosting servers is 403 Forbidden:
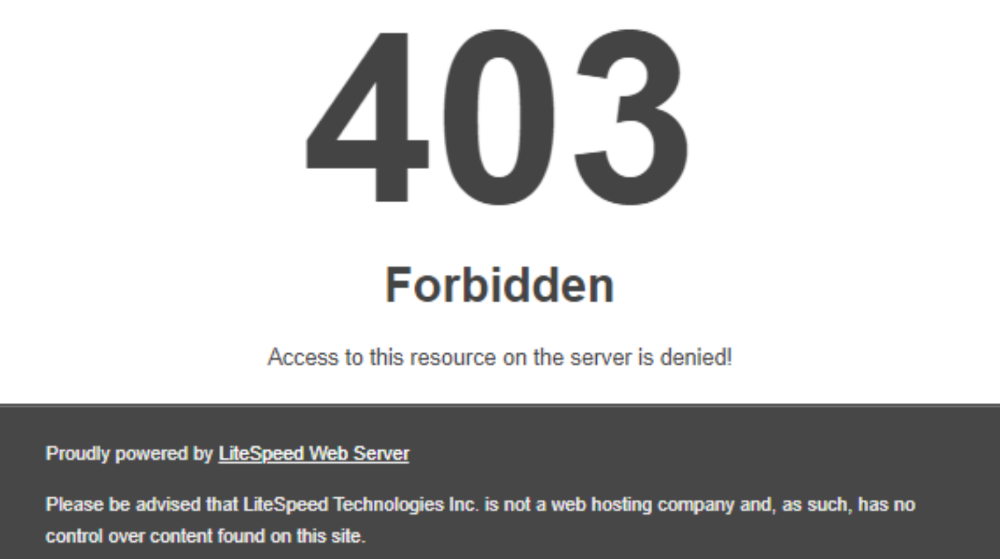
It means that you do not have permission to access specific resource or a path of the server. Depending on the exact link where you get the error, the path could be different.
When ModSecurity is on, you should know that it works in the background and you can not notice it. Also, every single page request is being checked against various rules to filter out those requests which seem malicious - the ones that have been run to exploit vulnerabilities in your websites or web-based applications with the only goal to hack the them.
There are also scenarios where due to poor website coding, ModSecurity may incorrectly and without any announce determine that a certain request is malicious, while it is actually legitimate. If this happens, you will still get a 403 error.
Important:
Instead of getting the 403 Forbidden error, you may also receive 404 Not Found or 500 Internal Server Error errors. So, keep in mind that checking ModSecurity should be one of the options when you get such errors.
If ModSecurity, or also known as mod_security, rules are triggered too often on your websites, the corresponding IP address (the one those requests are sent from) will be blocked by the server firewall. This will result in your control panel being completely unavailable from this IP.
You should know that ModSecurity rules can be whitelisted or disabled by yourself, or by our support team. It can be done for a specific domain name, but you should keep in mind that this could bring some risks once the specified rule is disabled or ModSecurity is turned off.
Steps to disable mod_security rules
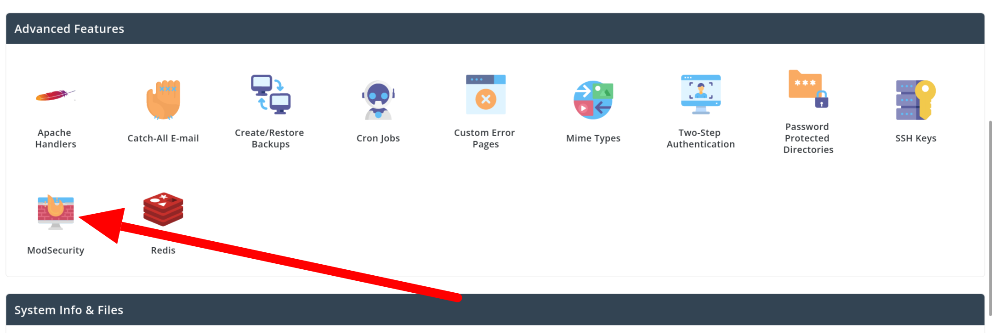
- Login to your control panel.
- Go to ModSecurity application.
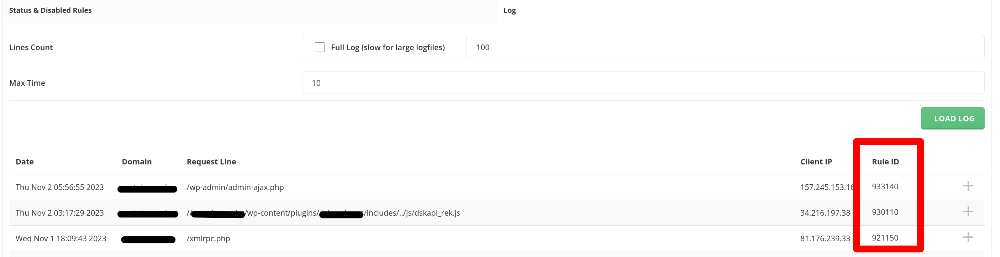
- Navigate to Log tab and see if there are new rules generated.
Also, it could look like this:
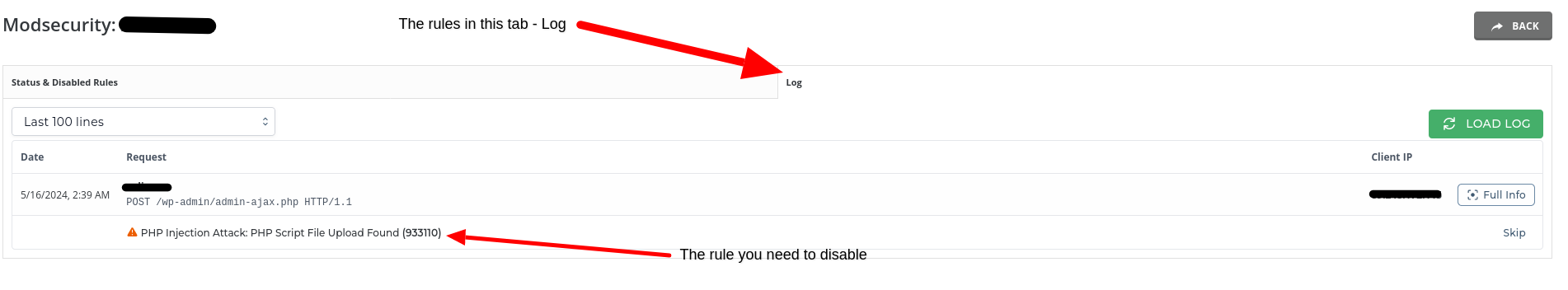
- Copy the ID of the rule(s) and paste it / them to the disable filed, and press Disable Rule.

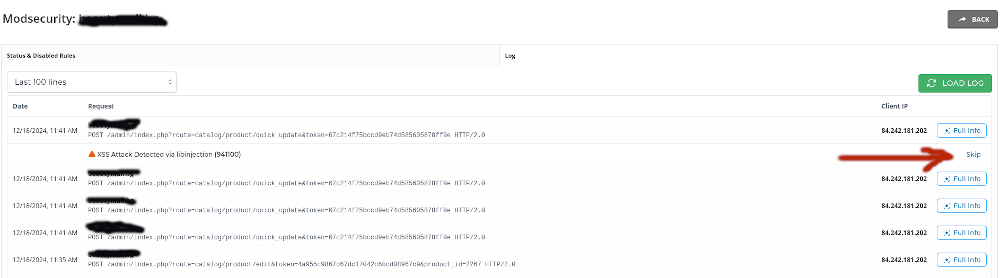
- Now you are done. You can disable one rule or several rules, depending on which of them prings the error of your websites.
- Note that this functionality is per domain name, so you need to see on which domian you are adding this rule.
- Keep in mind that the errors could be seen in the Error section in your control panel as well.
A ways to detect mod_security block are as follows:
- 403 Forbidden, 500 Internal Server Error, 404 Not Found errors are shown on your website frontend or backend when performing certain actions/requests. Page reloading, saving content, uploading image and more.
- The way to reproduce the error is usually the same all the time. mod_security blocks a certain activity only and nothing more.
- The other functionality on your website frontend and / or backend remains normal.
- As we mentioned, the error log for the specific domian generate it in the logs.
Now you know how ModSecurity works and you can prevent any future errors generated by this module.